Today, organisations are increasingly vulnerable to insider threats, which can cause significant operational, organisational, and reputational damage. It’s essential to have a comprehensive understanding of insider risks, threats, and gaps in your defences.
Our Approach
We believe in a collaborative approach that emphasises understanding our clients’ business, organisation, and culture. This method helps us deliver well-founded assessments and recommendations, secure top-management buy-in, and promote good practices in Insider Risk Management (IRM).
We can provide:
- An informed and calibrated assessment of IRM maturity.
- A robust evaluation of the insider threat environment impacting the organisation, its customers, and Critical Third Party (CTP) suppliers.
IRM Services
GSA Global helps businesses to strengthen their security and resilience against fast growing insider, cyber and physical threats. GSA Global brings a unique blend of human, technical, cyber and physical risk management experience that allows us to provide unparalleled insight and expertise in:
- Advising on the threats now facing our clients and the risks to their businesses
- Advising on the appropriate, proportionate and practical defences that are now needed
- Investigating suspected insider incidents
- Advising on and supporting the implementation of technology to monitor and mitigate insider risks
- Providing employee, contractor and third-party vetting
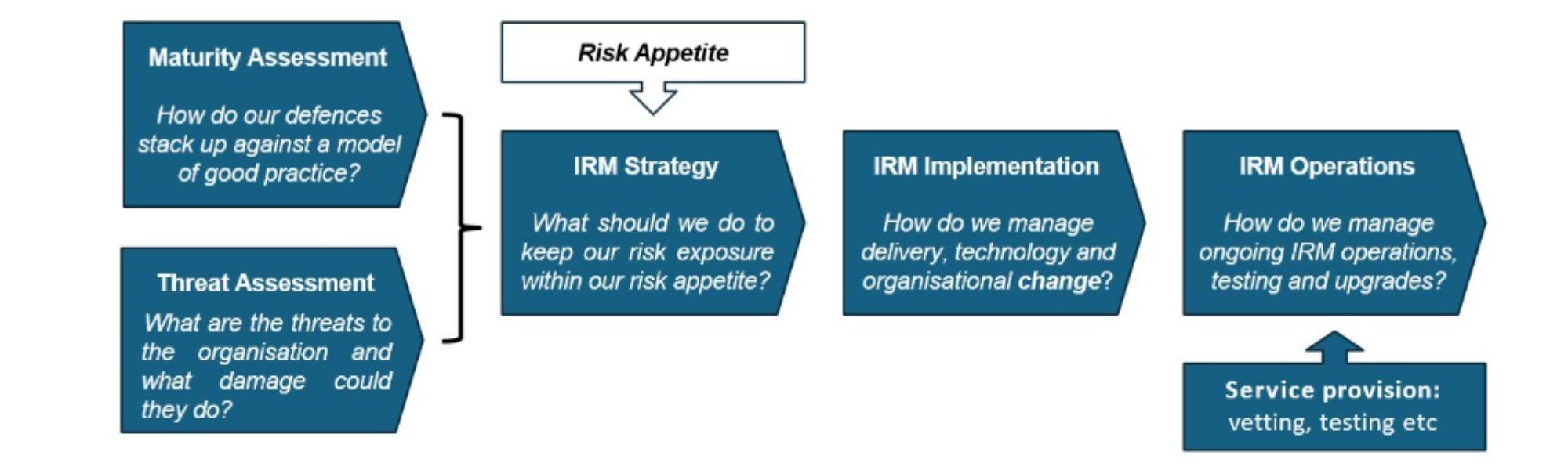
The IRM journey with GSA
GSA works closely with clients as they develop their insider risk strategy and operations. We have the insights and capability to help from the start, in understanding threats and risks, helping to formulate robust and pragmatic strategies and implementation plans; all the way through to supporting ongoing IRM operations.
Insider Risk Management “Snapshot” Tool
To help businesses understand the increasingly complex and multidisciplinary challenges of defending against insider attacks, GSA Global has developed a free, simple and user-friendly IRM Snapshot tool to help board members, business executives and functional leaders explore current IRM challenges through consideration of practical scenarios. The Snapshot is arranged in sections so that a board member, executive or functional head can explore a handful of scenarios that directly impact them.
Insider Threat Assessment
We work closely with clients to understand their business, their operating platform and organisation, and the potential for malicious, deliberate and/or inadvertent insiders to directly, or indirectly, facilitate the loss of data and/or the disruption of business operations. We enrich our assessment with the use of a broad range of open-source intelligence and our proprietary insight to develop a comprehensive picture of potential insider threats. These assessments deliver a robust overview of the level of threat to the business with a number of plausible but severe scenarios that help illustrate the potential for damage that could realistically be imposed by insiders.
This helps top management understand the scale and severity of insider risks and thereby set appropriate and proportionate targets for the insider risk management strategy – putting insider risk management into a broader business risk management context. This in turn helps to ensure that boards, top management and HR, Cyber, Physical Security and other functional teams have a shared understanding of insider threats.
Insider Risk Maturity Assessment
We work closely and collaboratively with clients to understand all the organisational, operational and technical contributions to insider risk management. We draw on our extensive experience and work in developing guidance on good practices to provide an insightful and measured assessment of how all of the contributors to insider risk management stack up against emerging good practices, and how they combine to deliver institutionally effective insider risk management.
This helps boards, top management and the leaders of key functional teams understand the need for change in IRM strategy, organisation and technical defences. In particular, it helps our clients shape an appropriate, robust and pragmatic approach to dealing with the most pressing new and fast-growing threats such as the threat from insiders in critical third parties.
Insider Incident Investigation
Insider incidents can vary greatly in sophistication, complexity and impact upon an organisation’s operations, resources and reputation. Within parameters defined and agreed with our clients, we provide human and technical investigative support to help clients identify and hold to account those responsible for harm or loss.
For further information about any of IRM services contact us at [email protected]
Case Studies
Supplier to the oil industry
Investors in the company were concerned that expected profits were not materialising despite exceeding revenue targets. GSA were called to investigate. It was discovered that an insider responsible for procuring high value equipment used agents as intermediaries, adding significant costs and reducing profits by tens of millions. Litigation followed and GSA provided expert evidence.
Global software company
A major software company was acquired for $1b and concerns were raised regarding sales
contracts. GSA was asked to investigate. The investigation discovered a major fraud by a senior employee where sales and service contracts worth tens of millions of dollars were entered into with paper companies. GSA developed a comprehensive remediation plan and supported litigation to mitigate losses.
Major global bank
Senior executives and regulators became concerned about trading staff conduct in certain global banks. GSA staff were engaged to investigate, assess the scale of the problem and provide advice on strengthening defences against employee and counterparty misconduct.
